Best Practices for Securing APIs : Stay Ahead of New Threats
APIs are more important than ever in 2025, but they’re also more insecure. The proliferation of cloud native apps, microservices, IoT and AI integrations has made APIs the foundation of digital infrastructure. However, as APIs have grown in popularity, so too have cyberattacks that target them.
Whether you’re creating internal services for your company or public APIs for mobile apps, protecting them is crucial. These are the best practices for API security that every product team, DevOps engineer and developer should adhere to in 2025.
1. Implement an architecture with zero trust.
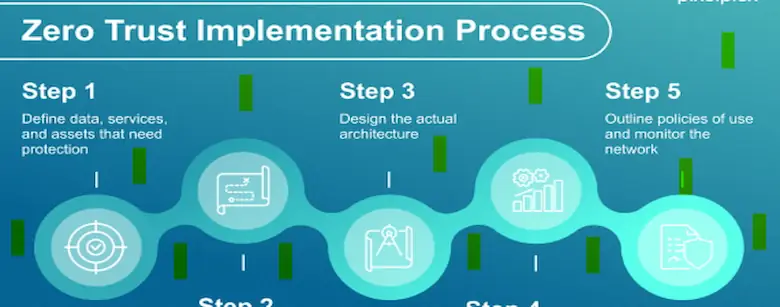
The “trust but verify” approach is no longer relevant. Zero Trust is the foundation of today’s API security approach, which holds that no user or client is reliable by default not even behind your firewall.
- For each request use permission and authentication.
- Put least privilege access constraints in place.
- Separate services and confirm each request.
For token-based access and identity management use OpenID Connect or OAuth 2.1 in conjunction with Zero Trust.
2. Employ Robust Authorization and Authentication
Simple API keys are no longer sufficient to protect against increasingly complex API assaults.
- Use OAuth 2.1 tokens or JWT (JSON Web Tokens).
- Define what a user or service may access by implementing roles and scopes.
- Rotate secrets and tokens on a regular basis.
Whenever feasible use multi-factor authentication (MFA) for external customers or third-party APIs.
3. Throttling and Rate Limiting

Rate limitation shields your API from denial-of-service (DoS) attacks, misuse, and bots.
- Put restrictions on each person, IP or app.
- Utilize rate restriction that is adaptable to traffic patterns.
- Use common HTTP codes to reply such as 429 An excessive number of requests
Additionally, this lessens the strain on the infrastructure and guarantees a more seamless experience for authorized users.
4. Track and Record APIs Activity
What you cannot see you cannot defend. Threat identification and auditing depend on API logging and monitoring.
- Record every API call error and attempt at authentication.
- Make use of programs like Cloud Watch, Datadog and Elastic Stack.
- Use anomaly detection to identify odd consumption trends.
By 2025, AI-powered threat detection is growing in popularity, employing behavior modeling to instantly identify questionable conduct.
5. Encrypt All Data, Both at Rest and in Transit

Make sure all endpoints utilize HTTPS with valid certificates and encrypt API communication using TLS 1.3 (Transport Layer Security).
- Never send private information in plain text such as tokens or passwords.
- Encrypt data and records kept in file systems or databases.
- Use SHA-256 or HMAC to sign answers and requests.
6. API scanning and security testing

As with web apps test and scan your APIs often for vulnerabilities.
- Make use of automated tools such as APIsec Burp Suite, or OWASP ZAP.
- To examine how your API responds to unforeseen inputs, conduct fuzz testing.
- Refer to the OWASP API Security Top 10 list for 2023–2024.
7. Make use of WAFs and API Gateways
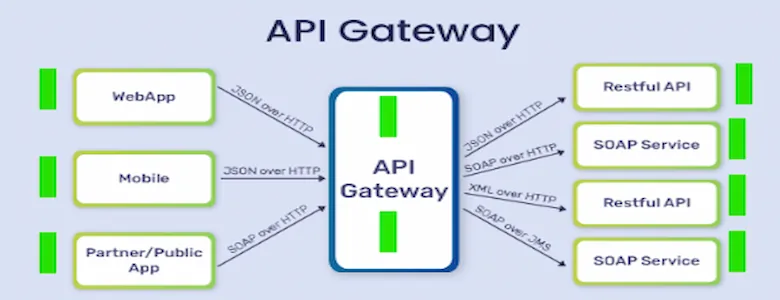
API gateways such as Kong Amazon API Gateway and Apigee serve as your APIs front entrance in 2025.
- Manage logging, rate limitation, authentication and other tasks.
- Block harmful requests by combining with a Web Application Firewall (WAF).
- Turn on schema enforcement and request validation.
Concluding remarks
The hazards rise as APIs become increasingly essential to services and apps. By 2025, API security is a business concern rather than only a development effort. You can protect user data, secure your APIs and increase the credibility of your digital goods by using these best practices.